The following scenario: You can be identified on the Internet at any time. No matter which browser you use. No matter which IP address you use. Even when you’re on the Tor network. This scenario has been a reality for five years. The tracking method is as simple as it is effective.

A new tracking method discovered by the security experts at FingerprintJS makes it possible to spy on users across browsers – even if anti-tracking measures are explicitly used. Neither another browser , incognito mode nor a VPN service can prevent tracking. Thanks to the procedure known as Scheme Flooding, third parties can specifically identify you and at the same time possibly even receive demographic data about you. Particularly explosive: Even the Tor browser , which was specially developed to preserve anonymity, did not offer any protection until recently .
SCHEME FLOODING: HOW THE TRACKING METHOD WORKS
Ever since home office and homeschooling became part of everyday life, everyone should be familiar with the small pop-up window that asks permission to open an application – for example Zoom, Slack, Steam or WhatsApp – from the browser .
As soon as such a pop-up window appears, JavaScript identifies it and the hacker knows that the corresponding application is installed on your computer. Now you have to imagine the following: Take 100 applications and check which of them are installed on your computer. This results in a specific application combination – comparable to an identification number – that can only be assigned to a few users or even only to you. And should the software discover the same combination in a different browser or even via a different IP, the hackers can still identify you.
Furthermore, such a combination of applications can of course also give certain indications of your demographic data. The majority of those who have installed the Internet distribution platform for computer games Steam on their computers, for example, are likely to be relatively young. Those who use Slack, on the other hand, would have to be mostly of working age. A combination of the two factors alone can filter out young adults, for example. And the more data you analyze, the more precise the user profile becomes, which third parties could then use for targeted advertising, for example.
The experts at FingerprintJS have created a demo website that reviews 24 applications. During our self-test, the website identified eight programs and then assigned us a unique number. This means that out of 62,974 tests to date, only we have shown this particular application combination. As a result, the software didn’t even identify us as part of a small group, but as individuals.
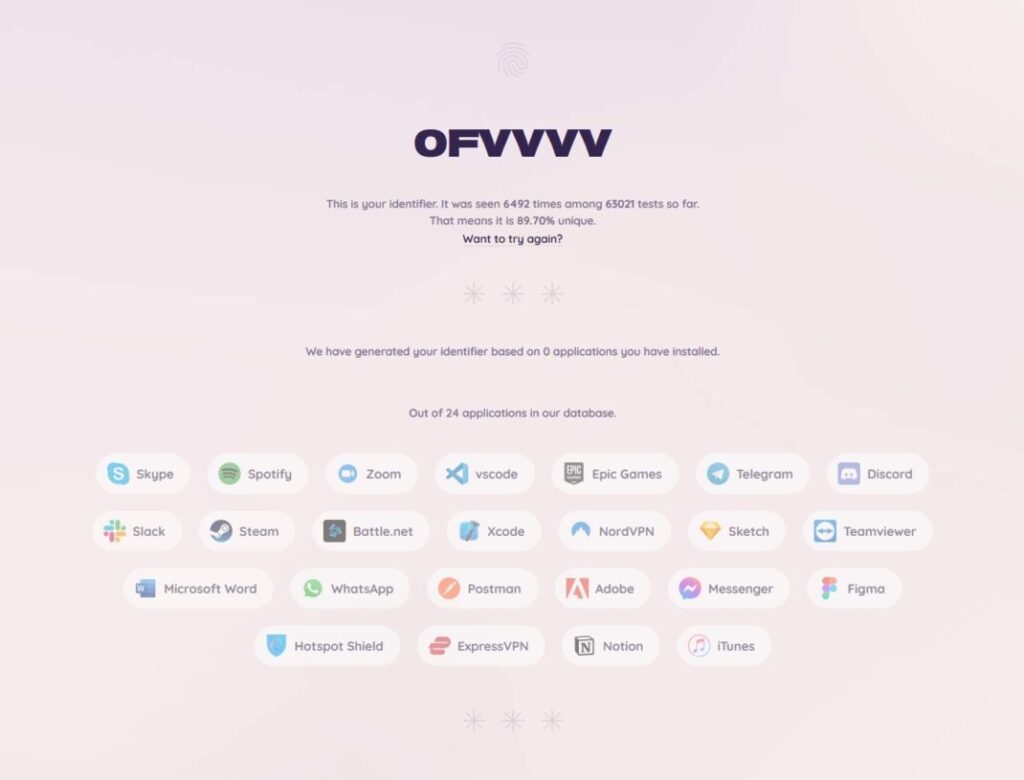
Scheme Flooding: New tracking method – in the Tor browser
ALL MAJOR BROWSERS ARE AFFECTED
Technically, the procedure described above varies slightly depending on the browser. However, according to FingerprintJS , neither Chrome, Safari, Firefox or Tor could offer sufficient protection. The security experts informed the associated companies, but so far only Tor has closed the gap. Users of the security browser are therefore advised to update to version number 10.0.17 as soon as possible. Otherwise, a second computer can currently offer protection from the vulnerability. However, it is not known whether third parties have already abused the browser vulnerabilities in practice.


